What is the ToolShell exploit?
Since July 18, 2025, several national agencies, CERT and cybersecurity companies have warned about attacks targeting SharePoint. Microsoft issued urgent advice about two serious vulnerabilities, CVE‑2025‑49704 and CVE‑2025‑49706, affecting on-premise SharePoint servers, which are being actively attacked. These two vulnerabilities are part of a very dangerous attack chain called ToolShell.
Since the initial patches from Microsoft for these vulnerabilities were not complete, new security patches for CVE-2025-53770 and CVE-2025-53771 have been released.
2 CVE, 1 attack chain, what’s the deal?
The ToolShell attack combined 2 vulnerabilities:
- CVE‑2025‑49706 (initial) and CVE‑2025‑53771 (update) let an unauthorized attacker access SharePoint without logging in. Attackers use the « ToolPane.aspx » endpoint with specially crafted HTTP requests and a specific Referer header to get around authentication. The Kaspersky team managed to bypass the initial fix for CVE‑2025‑49706 by adding just one byte to the exploit POST request. They only needed to add a “/” (slash) at the end of the “ToolPane.aspx” path. More details can be found at https://securelist.com/toolshell-explained/117045/.
- https://nvd.nist.gov/vuln/detail/CVE-2025-49706
- CVSS base score:
6.5(MEDIUM)
- CVSS base score:
- https://nvd.nist.gov/vuln/detail/CVE-2025-53771
- CVSS base score:
6.5(MEDIUM)
- CVSS base score:
- https://nvd.nist.gov/vuln/detail/CVE-2025-49706
- CVE‑2025‑49704 (initial) CVE‑2025‑53770 (update) lets an unauthorized attacker run arbitrary code remotely (RCE). This is a vulnerability caused by not properly checking XML data. For the first CVE, Microsoft didn’t fully fix the vulnerability; they just reduced the risk by adding the new AddExcelDataSetToSafeControls class to the Microsoft.SharePoint.Upgrade namespace (thanks to Kaspersky team analysis: https://securelist.com/toolshell-explained/117045/).
- https://nvd.nist.gov/vuln/detail/CVE-2025-49704
- CVSS base score:
8.8(HIGH)
- CVSS base score:
- https://nvd.nist.gov/vuln/detail/CVE-2025-53770
- CVSS base score:
9.8(CRITICAL)
- CVSS base score:
- https://nvd.nist.gov/vuln/detail/CVE-2025-49704
In summary, the first vulnerabilities (49704/49706) were fixed in July 2025, but new methods to exploit them were discovered, resulting in two new CVEs, 53770 and 53771.
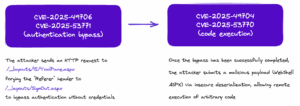
Simplified ToolShell Exploit Chain
Which products are affected?
The vulnerabilities only affect on-premises versions of Microsoft SharePoint Server. This includes servers on physical machines and self-managed SharePoint instances in the cloud.
The affected SharePoint versions are:
- Microsoft SharePoint Server Subscription Edition
- Microsoft SharePoint Server 2019
- Microsoft SharePoint Enterprise Server 2016
- SharePoint Server 2010 and 2013 are no longer supported, but Microsoft still lists them as affected. They will not receive updates from Microsoft.
Microsoft states that SharePoint Online in Microsoft 365 is NOT affected.
Observed exploitation
Several cybercriminal groups from China are exploiting these CVEs. The groups known to be actively using these vulnerabilities are: Linen Typhoon, Violet Typhoon, and Storm-2603. They are involved in using web shells, stealing MachineKey keys, and spreading Warlock or LockBit ransomware.
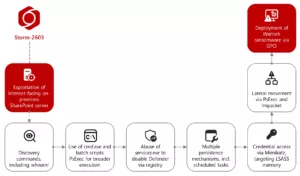
Storm-2603 attack chain exploiting SharePoint vulnerabilities and leading to ransomware
Source: Microsoft (https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities/)
Mitigation and protection guidance
Microsoft has detailed security recommendations on this page: https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities. The article includes a list of Indicators of Compromise (IOCs) from confirmed exploitation cases and queries to find possible exploitation activities; use these queries in Microsoft Defender XDR security center.
We also suggest checking the CISA bulletin for detailed recommendations (https://www.cisa.gov/news-events/alerts/2025/07/20/update-microsoft-releases-guidance-exploitation-sharepoint-vulnerabilities).
Other detection rules related to specific detection tools are also published:
- Eye Security article (https://research.eye.security/sharepoint-under-siege) provide a list of Indicators of Attack (IoAs) for hunting exploitation attempts with CrowdStrike Falcon, Defender for Endpoint, and Sentinel One Complete.
- PaloAlto provide XQL queries for Cortex XDR customers to search for signs of exploitation (https://unit42.paloaltonetworks.com/microsoft-sharepoint-cve-2025-49704-cve-2025-49706-cve-2025-53770).
Update on August 06, 2025: CISA published a Malware Analysis Report (MAR) with analysis and associated detection signatures on files related to Microsoft SharePoint vulnerabilities => https://www.cisa.gov/news-events/alerts/2025/08/06/cisa-releases-malware-analysis-report-associated-microsoft-sharepoint-vulnerabilities
Test your detection ability
We created a BlackNoise event to simulate this attack behaviors. It sends two web requests with non-working payloads to simulate the exploitation of CVE-2025-49706 and its new variant CVE-2025-53771. BlackNoise customers can use our solution to test how well they can detect this attack chain.
The detection of the first step in the attack can be done in several ways:
- Using Microsoft Defender XDR queries provided by Microsoft
- At the network level with tools like NDR or IPS/IDS (for example, using Suricata rules)
- Possibly at the endpoint level using a Sigma rule like the generic example next to it:
Note: Other methods can be used to find unusual behaviors linked to CVE‑2025‑49704 and CVE‑2025‑53770 (like Sigma rules, Yara, Sysmon, etc.), especially to spot Suspicious WebShell Execution.


